Strong passwords are important for keeping accounts secure, and we can make passwords so strong that it is impossible for hackers to try every possible combination. That’s the good news. The bad news is that criminals have adapted by developing methods for guessing more efficiently, and they have found ways to steal our passwords either from us or the service providers we use.
It doesn't matter if they steal a password or guess it, once a criminal has your password, they will use it to log into your account. And they know most people reuse passwords, so they will try that password for every account of yours they can find. Worse, they may sell that information to other criminals. Thus one breach can become many.
Stealing a password for one account, and then using it to login to another account, is called credential stuffing, and it has been a popular technique of criminals for many years. It only works because most people reuse passwords across multiple accounts. In fact, a survey found that, on average, people have four passwords for all of their accounts—that's a lot of password reuse!
A unique password is a password that is used for only one account. It's not strictly a property of the password itself, like length, complexity, and randomness are—rather it's about that password's relationship to all of your other passwords. Your bank may have strong security but if you are using the same password on your gym app, and the app has bad security, hackers can steal the password from the app and then login to your bank account. And if they get the password for your email account, it's disastrous because from there they can reset the password for every account that doesn't require multi-factor authentication. This is why using unique passwords is important: it stops one breach from turning into many.
Like bulkheads on a ship, password uniqueness is about containing damage. The trade off is that we have to find ways to memorize or manage all of these different passwords, but it is necessary because hackers have gotten very good at stealing and guessing passwords.
Providers Cannot be Trusted
How do hackers have access to so many passwords? We would like to believe that the companies behind the apps we use have good security--or at least decent security. But research has shown that developers who make our apps often are unaware of what constitutes good security. And even when they do, companies are in the business of making money, and security often takes a backseat to profits.
RockYou was a tech company in San Francisco that made a lot of money developing games for Facebook, MySpace, and other social media platforms. In December 2009, they suffered a major data breach where the usernames and passwords of 32 million accounts were stolen. Worse, it turns out a they had put *zero* security on users' passwords-- the passwords were stored in plain-text, meaning the attackers could read them without any additional work.
After it was stolen, RockYou’s password database was shared around the world via the dark web, and it became a windfall for criminals who used these passwords in credential stuffing attacks. This was bad, but it turns out RockYou was not alone. In 2016, Yahoo! disclosed two separate attacks that collectively exposed 3 billion accounts. It turns out many passwords had weak security on them and some accounts had the answers to security questions stored in plain-text. To compound the damage, Yahoo! waited over two years to notify users, leaving them vulnerable to credential stuffing attacks with no way to know they had been exposed.
The list goes on. Sony, Adobe, LinkedIn, Facebook, Twitter, GoDaddy, MailChimp, LastPass, and many, many others have all had breaches that exposed passwords or other login data, fueling large scale credential-stuffing attacks.
Unfortunately in the United States, unlike the EU, there is no uniform regulatory requirement to notify affected parties, which means we cannot rely on vendors to notify us of a breach at all, let alone in time for us to protect ourselves. Yahoo! waited over two years notify users, and while that is an outlier, in 2024 Ticket Master took six months to notify users that data from a breach was for sale on the dark web. That same year Goosehead Insurance and Conduent Business Solutions suffered breaches as well, and Goosehead waited seven months to notify affected parties, while Conduent took ten months to notify users that their accounts were exposed.
Breach Frequency
So how bad is it? Verizon Data Breach Investigations Report identified 12,195 breaches in 2024. During that period IBM’s X-Force observed a 12% increase year-over-year in the number of listings for stolen credentials. Research has estimated that, as a conservative estimate, 82% of Americans have had their accounts exposed, while the average person has had least 3 accounts exposed.
My password manager shows me that I have about 300 online accounts; which suggests that there is a 95.1% chance that at least one of my accounts has been exposed during the account’s lifetime, and every year there is a 59.4% chance every that one of my accounts is leaked. Leaked doesn’t necessarily mean a hacker knows my password, but rather that it ended up in a stolen database. And the problem is we don’t know how good the security on the exposed passwords is.
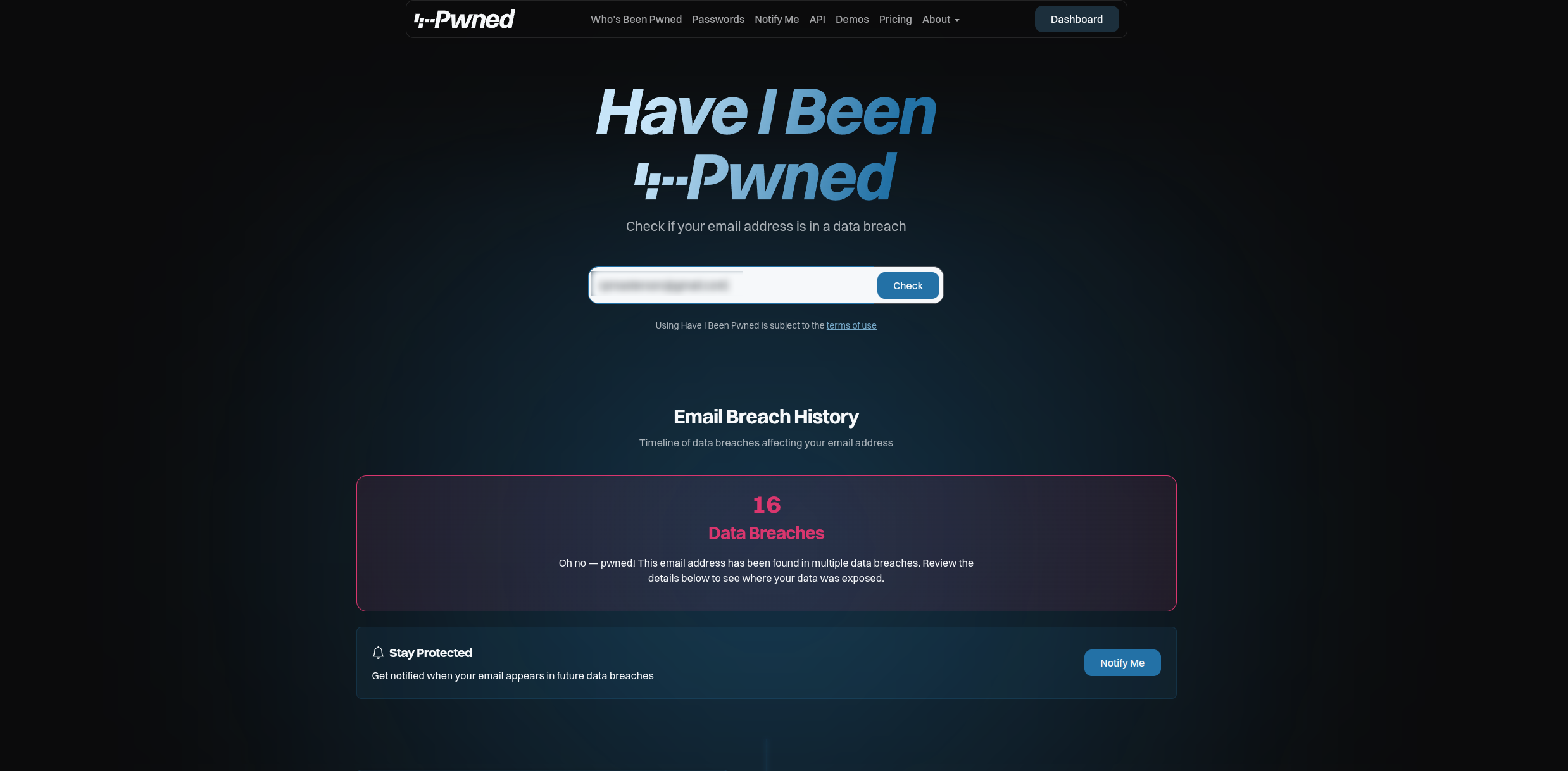
You can check to see if an account has been exposed at haveibeenpwned.com. It turns out that my personal email address has been in 16 data breaches, and I've had the account for approximately 20 years. But many breaches are never publicly disclosed, sometimes Have I Been Pwned is legally prevented from including a breach in its dataset, and at other times it intentionally limits what they report for security reasons. The take away is that this is a lower-bound, and the number of times an account has been exposed will be higher.
Guidance
Breaches are a frequent reality of life in the modern digital era and we can't trust vendors to protect our account information or inform us when our account has been exposed. The odds are not in our favor. For these reasons, it is important to use unique passwords which prevents a single breach from exposing a multitude of accounts.
Yet there is simply no way we can do this on our own. Our memories are not up to the task, which is why we should use a password manager to generate, store, and enter the passwords for us. Password managers can generate strong passwords and they make it easy to have a unique password for each account. They are an essential tool for cybersecurity so we'll take a look at those next.