Accounts are protected by passwords, which we are required to know to get into our accounts and access a service and its related data. Criminals will try to guess your password to gain access to your account, so it's important to use a password that is difficult for someone to guess. Some passwords are strong while others are weak. Password strength reflects how long it will take someone to guess the password, so it's important to have strong passwords.
There are two ways that criminals try to guess your passwords: online and offline. In an online attack they input a password into a password field just like you do and click "log in" and wait for a response. If their guess is wrong, they try the next password on their list, and they'll keep guessing until they get in.
Online services tend to limit how fast a criminal can enter passwords and then lock them out after a certain number of failed attempts. This means that criminals are limited in how many passwords they can try in an hour.
Offline attacks are where they hack into a website or a service provider and steal the database of user passwords. Most companies protect passwords in their databases so that criminals can't use them right away and still have to guess them. But in an offline attack there is no rate limit or timeouts, so attackers can guess passwords as fast as their hardware permits. Some vendors use techniques that deliberately slow down each guess, but users usually don’t know which vendors do this and which don’t. If a vendor doesn’t slow the attacker down, then security depends entirely on the strength of the password.
So what makes a password "strong"? It's really three factors: the password's length, complexity, and randomness.
Length
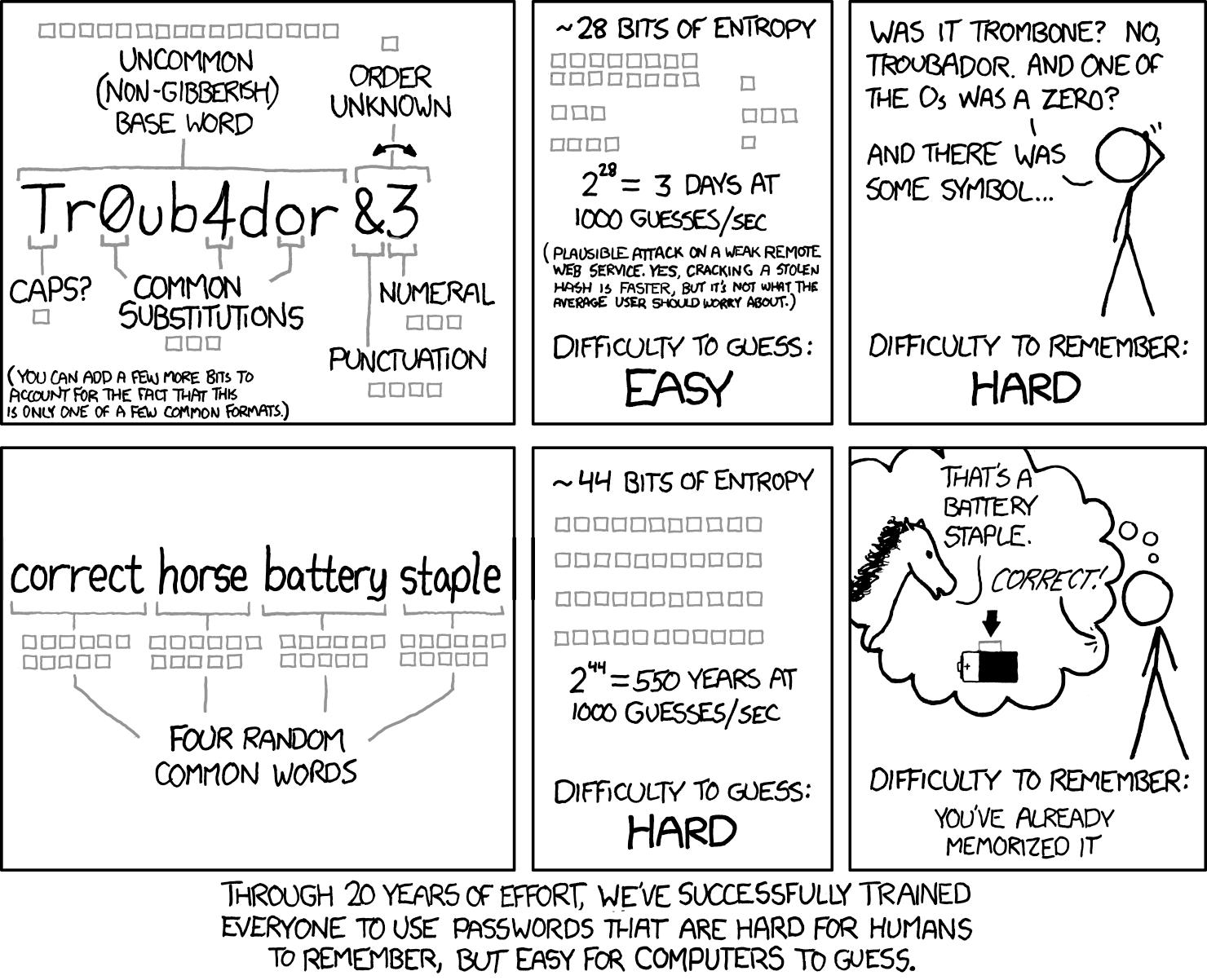
The single most important factor in a password’s strength is its length. That surprises a lot of people because *for decades* we were told a strong password had to have an upper case letter, lower case letter, a number, and at least one symbol. Some websites didn't even have a minimum password length (like WordPress!)
But it turns out that advice focused on the wrong thing. What really makes a password hard to crack (guess) isn’t how many symbols it has — it’s how long it is. Every extra character you add to a password increases the number of possible combinations dramatically. This means that long passwords quickly become impractical for attackers to guess, there are just too many possibilities.
A comic from a former NASA programmer, Randall Munroe, illustrates this rather well:
The comment at the bottom is the take away-- for almost thirsty years we were told to use passwords that are difficult for us to remember but easy for computers to guess.
The importance of a password's length is reflected in the latest guidance from the National Institute of Standards and Technology (NIST). NIST is U.S. federal agency tasked with creating cybersecurity standards that federal agencies — and the U.S. military — are required to follow. They set the security for the most targeted systems in the world, so they know a thing or two about security! And for the past ten to fifteen years they have emphasized that longer passwords are stronger passwords.
Complexity
Complexity is the range of possible values that each symbol or digit in a password can have. The larger the range of possible values, the more combinations attackers have to try. Your traditional credit card PIN number has a length of 4 and complexity of 10 (the numbers 0-9). That means there are 10,000 possible combinations. If you swapped numbers for letters and made the pin case sensitive ( 'a' and 'A' are treated as different) you'd have a complexity of 52. A 4-character PIN with a complexity of 52 has over 7.3 million possible combinations. So the complexity of a password is powerful, just not as powerful as the length. Still, given equal length, a complex password will be significantly harder to guess than a simple password.
Randomness (Entropy)
The last aspect of password strength is it's randomness (entropy is a measure of randomness). Passwords that are easy to remember are easy to guess. The more random a password is, the harder it is to guess. If you use your name, your email address, your pet's name, the website's name, common words, etc. it makes your password easier to guess. There are large dictionaries available on the dark-web that contain the most commonly used words found in passwords and criminals will use these dictionaries to guess your password faster. Modifying the words doesn't help because attackers use programs that will guess all the common alterations and substitutions derived from those words. So if you are using known words, even with substitutions or alterations, that word is almost certainly in an attacker's dictionary and their programs reduce how long it takes them to guess your password. To avoid using common words, random passwords are best. This makes one of their most powerful tools ineffective.
Unfortunately random is hard for people to remember, so we don't like random. McDonald's was recently caught using the password "123456" on a system handling job applications. Not surprisingly, the personal information of millions of job applicants was exposed because of this absurdly weak password. Apparently they didn't learn their lesson from President Skroob in Spaceballs whose luggage combination was 12345. And McDonald's is not alone! Back in 2009 a data breach at a popular game vendor revealed that almost 300,000 people were using "12345" as their password.
Human, all too Human
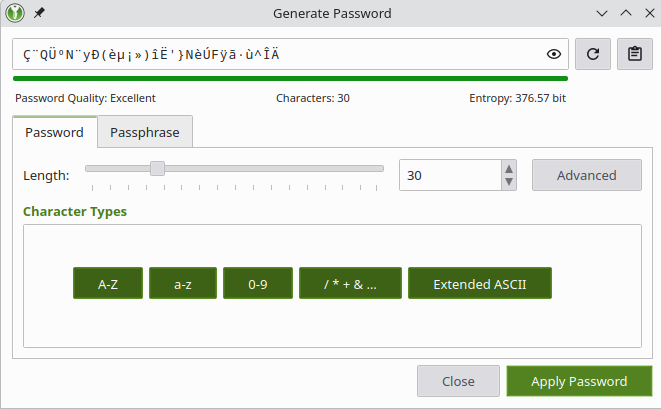
So a password's strength is a combination of its length, complexity, and randomness. The best passwords are at least twenty characters long, highly random, and highly complex. We can use entropy to approximate how strong a password is. It is possible to make passwords that are unbreakable even with the most advanced equipment. But they look like the password in this photo.
Such a password (376 bits of entropy) would take several times the age of the universe to crack even at 1 trillion guesses per second.^[4.87 x 10^93 years to crack with blind guessing at a trillion guesses per second. The universe is 13 Billion years or 1.38×10^10 years by comparison.]
But now that we know what makes a strong password, there is a fairly obvious problem-- us. Only someone with a photographic memory could memorize this password, and even then they'd give up trying to type it.
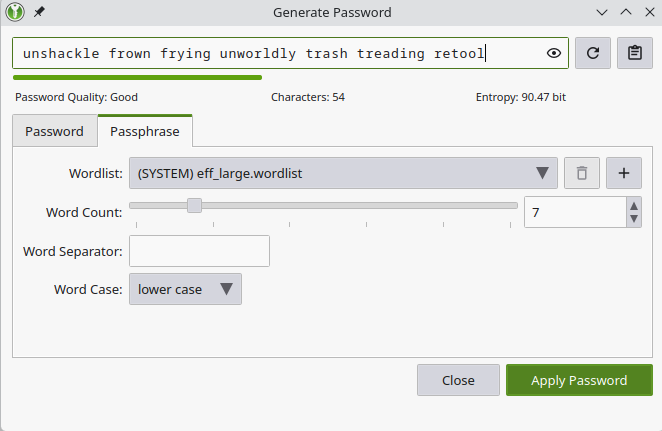
Now 370 bits of entropy is overkill-- a password with between 80 and 100 bits of entropy is strong enough in most cases, like the passphrase in this second image, which has approximately 90 bits of entropy. Still this password is 54 characters long and most of us would struggle to memorize it or type it in correctly. Can you imagine making a typo half way through and having to start over? Or having many passphrases? You would start confusing words from one phrase with words from another phrase.
There is no sugar coating it: we are the weakest link when it comes to password security. Fortunately, there are tools like password managers that can help us use strong passwords, and not lose our sanity trying to memorize them or type them. They come with their own pros and cons so we'll take a look at them as well, but first we'll discuss why it's not a good idea to memorize one or two really strong passwords and use them for every account.